GoldKey Hierarchical Management
with b² cryptography
A Breakthrough Innovation for Encryption Key Distribution and Management
Unlike PKI, widely used to secure systems today, b² cryptography reliably authenticates the user to a service, and authenticates the service to the user. b² cryptography cracks the age old problem of securely sharing encryption keys, even over hostile and public networks.

Hardware-based b² cryptography
b² cryptography is based on the use of a hierarchal, hardware-based structure which facilitates the sharing and management of strong encryption keys. It also provides a robust solution to the long standing need for reliable user authentication. Unlike its predecessors, b² cryptography automatically authenticates the user to the service and the service to the user eliminating dangerous man-in-the-middle and phishing attacks.
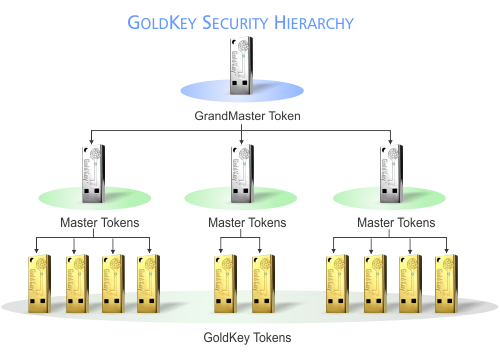
The b² cryptography hierarchical structure can be used to delegate access privileges from upper management down to each individual user. This hierarchical management defines clear pathways to enforce access policies to secure resources and services. These pathways empower managers to make role-based access decisions at mission speed, without the intervention of IT. In this same way, managers have the ability to revoke access and take back delegated authority.
b² cryptography is a hardware-based key management system utilizing strong encryption with military grade, AES 256 bit symmetrical keys. To qualify as a hardware-based key management system, keys must be generated with a hardware-based random number generator. Keys generated by software are not completely randomized and are therefore more vulnerable to brute force and other attacks. In addition, the system must provide a robust system of key distribution, revocation, and renewal that is not prone to the vulnerabilities of current software-based key management solutions.
Not only are these systems secure, they are also fast, running as much as 20 times faster on a given piece of hardware than asymmetrical encryption alternatives.
Though an effective solution when invented 20 years ago, one-time passwords and certificate-based security is now vulnerable to brute force attacks and is no longer a good data protection solution.
GoldKey USB Tokens
GoldKey security tokens are based on b² cryptography. Inside each GoldKey USB token, is a powerful random number generator that is used to create keys for strong encryption. In addition to the hardware random number generator, each GoldKey contains a powerful security processor. The GoldKey token also provides the hardware management system that allows users to set up their own security infrastructure that provides private key management to all of their computers allowing them to store files in the cloud, on local drives, or in secure vaults with the peace of mind that NO ONE will be able to gain access to their data.

b² cryptography provides the capability of managing symmetrical encryption keys securely, even over a network connection. This is done by creating a private security hierarchy for each user. With the private hierarchy, it is possible to create a very secure connection over the network. Since this very secure connection is established with b² cryptography, the resulting secure connection is referred to as a Gold Pipe. Once the Gold Pipe has been established, it can be utilized to efficiently encrypt and transfer all types of data securely between devices.

Group Solutions
In applications that require that groups of users have the ability of sharing encrypted files, a group security hierarchy can also be created. Group security hierarchies are created with a GoldKey Master token. Master tokens can manage and disable GoldKey Card or USB tokens which have been registered to the Master during setup. Registered users can then be granted access to specified files under the control of the Master. The Master can also block access of any user to any files as circumstances may require.
GoldKey tokens are used to manage access throughout organizations including group access to GoldKey Vaults, secure email, and other online accounts. Master tokens can be used to review access logs, unlock files encrypted by registered user tokens, and issue replacements of registered GoldKey tokens when needed.
